Why is Cybersecurity in Mining More Important Now than Ever? - The Race to Secure Critical Minerals
If you work in cybersecurity in mining, it is easy to forget why we do what we do. We are not in the cybersecurity business; we are not merely...
Threat intelligence can be extremely valuable for informing business decisions and strategies beyond detection and response, enabling agility in responding to the current landscape and developing resiliency for your operations. To use threat intelligence to inform business decisions, we must move past IOCs and examine the behaviours of threat actors targeting our industry.
At MM-ISAC, we’ve seen a newer trend of threat actors waiting months before releasing the data from an incident. I want to share some insight on why this might be happening and what companies need to know to avoid the headache and pain that may follow.
Previously, threat actors would give companies a time limit to pay a ransom and then threaten to release the information as additional leverage to get payment. The tactic threat actors are now taking is to hold exfiltrated data for weeks or even months before releasing it to the public or publishing it on their site.
It’s been nine months? Why wait so long to dump the data? Doesn’t that sound counterintuitive for ransomware groups to get paid? We will discuss a few reasons why, as well as discuss what you should be doing to prepare for this type of predicament.
This strategy creates two incidents for the price of one. The first incident is the initial breach, its impacts, and associated clean-up. The second incident involves releasing sensitive and confidential information that is accessible to the world to see. If the dump happened shortly after the breach, it would be one incident in the public eye. By waiting weeks or months later, the attacker returns the company to the spotlight for a second round of news headlines and stakeholder questions. The kicker is that it doesn’t have to be the same threat actor in round two. Alternatively, the stolen data could be sold to the highest bidder to run a second round of ransom demands and negotiations.
It’s business. Sometimes, it’s not about the company but more about the threat actor building a reputation and getting the next victim to pay up. The ransomware group never expected a payment from your company, but they’ve got enough to get you into a little hot water over confidential or private information. If they can make it as uncomfortable as possible – or downright a nightmare- they can use that as a cautionary tale to get the next victim to pay to avoid that whole mess.
During and after a breach, threat actors are watching your company very closely and see what kinds of communication are being put out, if any. Failure to disclose a breach to stakeholders, the SEC, and other requirements grants the threat actors the opportunity to make those disclosures on your behalf, with the reinforcing message “This company does not care about cyber security or their employees.”
Threat actors are opportunistic – So take away the opportunity. Disclose the breach first and beat them to the punch. Gone are the days when companies can quietly have an incident and hope nobody notices, especially stakeholders and investors. Incidents are commonplace; everyone gets a turn. More often than not, the company’s stock prices barely take a hit after a well-written press release and appropriate actions.
Cyber attacks are scary, and it is the fear of the unknown, the fear of losing public trust, and damage to reputation. But what stings more is when a company pretends everything is ok, word gets out that employee data and sensitive information were leaked, and the first time people hear about it is in a news headline stating that their information is on the dark web or the clear internet. Public trust is lost, and people feel lied to and angry about the lack of communication from corporate communications.
Incidents today no longer have the choice of whether or not to disclose a breach. The choice is now who makes the disclosure and when. Will it be by you at the time of the incident – or by the threat actor at whatever time they deem most effective to maximize impact?
Have a strategy for communicating a breach long before the first alert pops up that there is an issue. Disclose early in the incident with a clear message that the situation is being investigated and people are being notified accordingly. Show that you are in control. This takes the power away, and you get to control the narrative of how your company responds to security incidents.

If you work in cybersecurity in mining, it is easy to forget why we do what we do. We are not in the cybersecurity business; we are not merely...

This article will be the first of a series on how centuries-old techniques in interpretation – Hermeneutics can be used to interpret information to...
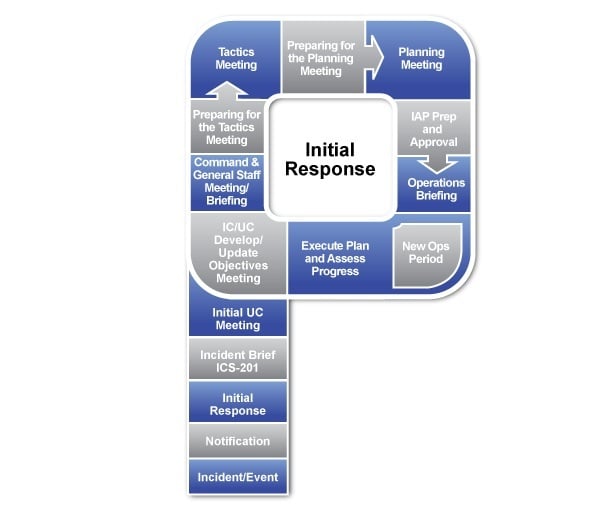
Cyber incident response is often viewed as a technical domain, with practitioners skilled in malware reverse engineering, network and host forensics,...